Cisco’s latest additions to their “next-generation” firewall family are the ASA 5506-X, 5508-X, 5516-X and 5585-X with FirePOWER modules. The new “X” product line incorporated the industry leading IPS technologies, provides next-generation Intrusion Prevention (NGIPS), Application Visibility and Control (AVC), Advanced Malware Protection (AMP) and URL Filtering. In the basic Cisco ASA 5506-x Configuration example, we will cover the fundamentals to setup an ASA firewall for a typical business network. FirePOWER module configuration is covered in a separate document. For a more comprehensive, multi-DMZ network configuration example please sees: Cisco ASA 5506-X FirePOWER Module Configuration Example Part 1-4.
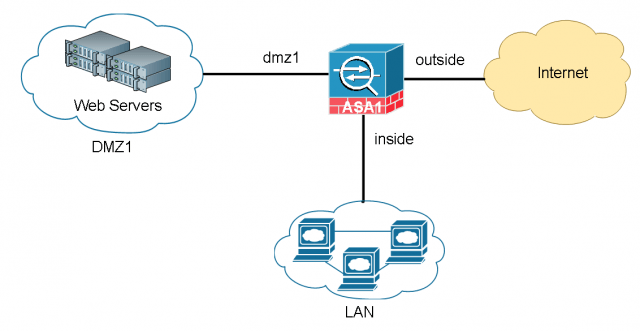
Below is the network topology that this example is based on. We will cover how to configure basic ACL (Access Control List), Network Address Translation (NAT) and a simple DMZ network hosting WWW server. The equipment used in this example is Cisco ASA 5506-X with FirePOWER module, running code 9.5(2).
You can download the entire lab setup and configuration files for FREE.
As part of our documentation effort, we maintain current and accurate information we provided. Documentations are routinely reviewed and updated. We ask for your email address to keep you notified when the article is updated.
Basic Cisco ASA 5506-x Configuration Example
Network Requirements
In a typical business environment, the network is comprised of three segments – Internet, user LAN and optionally a DMZ network. The DMZ network is used to host publically accessible servers such as web server, Email server and so on. The Cisco ASA acts as a Firewall, as well as an Internet gateway.
- LAN users and Web Servers all have Internet access.
- LAN users have full access to the Web Server network segment (DMZ1) but DMZ1 does not have any access to the LAN (in case DMZ is compromised).
- Anyone on the Internet can access the Web Server via a publically NAT’d IP address over HTTP.
- All other traffic is denied unless explicitly allowed.
Update ASA software and ASDM code
Download the recent stable release from Cisco.com and transfer the codes to the ASA.
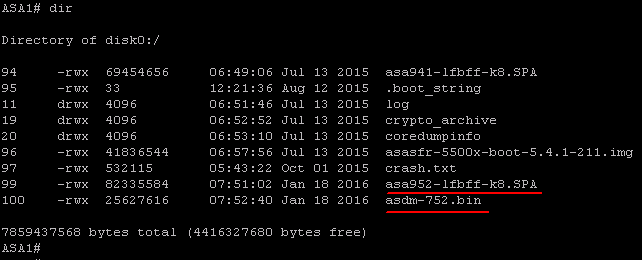
Set the system to boot to the new image. Configure the ASDM image to be used.
ASA1(config)# boot system disk0:/asa952-lfbff-k8.SPA
ASA1(config)# asdm image disk0:/asdm-752.binWrite memory and verify the bootvar is set correctly. Reboot the system to load the new image.
Security levels on Cisco ASA Firewall
Before jumping into the configuration, I’d like to briefly touch on how Cisco ASAs work in a multi-level security design. The concept is not Cisco specific. It applies to any other business grade firewalls.
By default, traffic passing from a lower to higher security level is denied. This can be overridden by an ACL applied to that lower security interface. Also the ASA, by default, will allow traffic from higher to lower security interfaces. This behavior can also be overridden with an ACL. The security levels are defined by numeric numbers between 0 and 100. 0 is often placed on the untrusted network such as Internet. And 100 is the most secured network. In our example we assign security levels as following: LAN = 100, DMZ1 = 50 and outside = 0.
LAN is considered the most secured network. It not only hosts internal user workstations as well as mission critical production servers. LAN users can reach other networks. However, no inbound access is allowed from any other networks unless explicitly allowed.
DMZ1 hosts public facing web servers. Any one on the Internet can reach the servers on TCP port 80 for HTTP.
The design idea here is that we don’t allow any possibilities of compromising the LAN. All “inbound” access to the LAN is denied unless the connection is initiated from the inside hosts. Servers in DMZ1 serve Internet web traffic and internal user traffic from the LAN.
Network Design and IP Assignment
For simplicity, we assume the SOHO network has less than 200 users and does not have a layer switch on the LAN. All user and server traffic point to the ASA as their default gateway to the Internet. We assign each network segment a /24 (255.255.255.0) subnet mask.
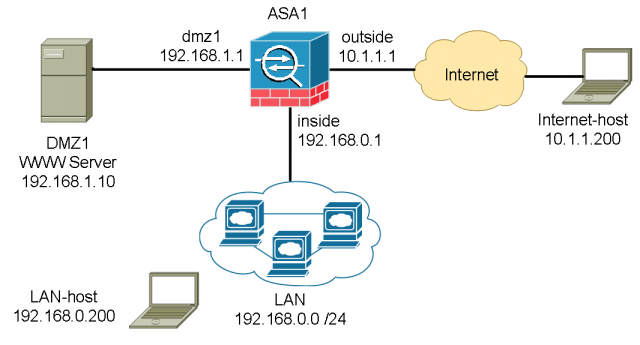
User LAN network:
Subnet: 192.168.0.0 /24
Gateway: 192.168.0.1 (ASA inside interface)
LAN-host (for testing): 192.168.0.200
DMZ1 network:
Subnet 192.168.1.0 /24
Gateway: 192.168.1.1
Web server: 192.168.1.10
Internet:
Internet-host (for testing): 10.1.1.200
Cisco ASA 5506-x Configuration
Step 1: Configure ASA interfaces and assign appropriate security levels
The ASA 5506-X comes with 8 GigE routed interfaces. We are going to use three of the interfaces in this network – inside (100), dmz1(50) and outside (0).
interface GigabitEthernet1/1
description to WAN
nameif outside
security-level 0
ip address 10.1.1.1 255.255.255.0
!
interface GigabitEthernet1/2
description to LAN
nameif inside
security-level 100
ip address 192.168.0.1 255.255.255.0
!
interface GigabitEthernet1/3
description to DMZ1
nameif dmz1
security-level 50
ip address 192.168.1.1 255.255.255.0Step 2: Configure ASA as an Internet gateway, enable Internet access
There are two things required in order for the internal hosts to go out to the Internet, configuring Network Address Translation (NAT) and routing all traffic to the ISP. You do not need an ACL because all outbound traffic is traversing from higher security level (inside and dmz1) to lower security level (outside).
nat (inside,outside) after-auto source dynamic any interface
nat (dmz1,outside) after-auto source dynamic any interfaceThe configuration above states that any traffic coming from inside and dmz1 network, translate the source IP to the outside interface’s IP for outbound Internet traffic. The “after-auto” keyword simply set this NAT the least preferred rule to be evaluated after Manual NAT and Auto NAT are evaluated. The reason we want to give it the least preference is to avoid possible conflict with other NAT rules.
Next is configuring a default gateway and route all traffic to the upstream ISP. 10.1.1.2 is the gateway the ISP provided.
route outside 0.0.0.0 0.0.0.0 10.1.1.2Also make sure “inspect icmp” is configured under global_policy. It allows icmp return traffic to pass the ASA while the Ping is initiated from inside hosts.
policy-map global_policy
class inspection_default
inspect icmpAt this point, you should be able to ping the host 10.1.1.200 on the Internet from any internal subnets.
Step 3: Configure static NAT to web servers, grant Internet inbound access to web servers
First we define two objects for the web server, one for its internal IP and one for its public facing IP.
object network WWW-EXT
host 10.1.1.10
!
object network WWW-INT
host 192.168.1.10
!
nat (dmz1,outside) source static WWW-INT WWW-EXTAnyone on the Internet trying to access the web server, they’ll use the public IP defined in WWW-EXT. It will be translated to the private IP defined in WWW-INT.
Now the IP address translation has been done. We will need to configure ACL and allow Internet inbound traffic to access the web server. And apply the ACL to the outside interface.
access-list OUTSIDE extended permit tcp any object WWW-INT eq www
access-list OUTSIDE extended permit icmp any4 any4 echo
access-group OUTSIDE in interface outsideThe ACL states, permit traffic from anywhere to the web server (WWW-INT: 192.168.1.10) on port 80. For troubleshooting and demonstration purpose, we also allow ICMP ping traffic. In a real-world network, I recommend disallow Ping for higher security.
Step 4: Configure DHCP service on the ASA
This step is optional. If you have a DHCP server on the LAN you can skip to the next step. For small businesses that do not have server in house, you may configure the ASA to be a DHCP server.
Specify a DHCP address pool and the interface for the client to connect. We reserve a few address before and after the pool for future network devices or appliances that require static IP.
dhcpd address 192.168.0.5-192.168.0.250 insideSpecify the IP address of the DNS servers for client use. It is always a good idea to have the secondary DNS server in case the primary fails.
dhcpd dns 9.9.9.9 4.2.2.2Specify the lease length to be granted to the client. This lease equals the amount of time (in seconds) the client can use its allocated IP address before the lease expires. Enter a value between 0 to 1,048,575.The default value is 3600 seconds.
dhcpd lease 3600
dhcpd ping_timeout 50Enable the DHCP service to listen for DHCP client requests on the enabled interface.
dhcpd enable inside
dhcprelay timeout 60(Optional) Step 5: Redirect traffic to the FirePOWER module for deeper level inspection
In order to utilize any of the ASA’s next-generation firewall features, Cisco made customers order subscription based licenses for the FirePOWER module to work. The subscription based licenses can be purchased annually, 3 or 5 years with discount. Here are list of licenses available:
- Intrusion detection and prevention (IPS license)
- Application Visibility and Control (AVC)
- File control and advanced malware protection (AMP)
- Application, user, and URL control (URL Filtering)
- IPS license is required for the AVC, AMP and URL Filtering license.
If you have a FirePOWER feature license available and send traffic to the FirePOWER module for deeper level inspection, here is an example of send all traffic to FirePOWER. In case there was a software (in case of 5585-X, it is hardware) failure, bypass the FirePOWER module without inspection.
class-map global-class
match any
policy-map global_policy
class global-class
sfr fail-openStep 6: Hardening the device
Shutdown unused interfaces
interface GigabitEthernet1/4 through 1/8
shutdownEnable SSH access for admin
There are three steps to enable SSH access:
- Create a hostname for your ASA
- Generate a RSA key
- Configure SSH access to the ASA, and only allow from known IP/networks.
Configuration example:
ASA1(config)# hostname ASA1
ASA1(config)# crypto key generate rsa modulus 1024
WARNING: You have a RSA keypair already defined named <Default-RSA-Key>.
Do you really want to replace them? [yes/no]: yes
Keypair generation process begin. Please wait...! The IP subnets from where you trust to manage the ASA
ssh 12.2.1.0 255.255.255.0 outside
ssh 192.168.0.0 255.255.0.0 inside
ssh timeout 30
ssh version 2
aaa authentication ssh console LOCAL
Step 7: Configure time and enable logging
It is important to enable logging so we know what happened in case there was an incident. Make sure time is set correctly and timestamp is enabled while logging. In this example we enabled logging into the ASA’s buffer memory. The maximum log size can grow up to 512MB and then the oldest logs are overwritten. The logging level is set to “debugging”, which records everything in detailed level.
ASA1# clock set 12:05:00 Jan 22 2016
ASA1# clock timezone EST -5
ASA1# clock summer-time EST recurring
ASA1# logging enable
ASA1# logging timestamp
ASA1# logging buffer-size 512000
ASA1# logging buffered debuggingTo view logs, issue command “show logging” on the ASA.
For a more comprehensive, multi-DMZ network configuration example please read:
Cisco ASA DMZ Configuration Example
Cisco ASA FirePOWER Module Configuration Example Part 1- 4
You can download the entire lab setup and configuration files for FREE. The package includes:




- INSTRUCTIONS.pdf– Read this instruction first It covers what each downloaded file is for and how to use them.
- Basic Cisco ASA 5506-x Configuration Example.pdf – The article in PDF format for your offline reference.
- Cisco-ASA5506-config.txt – The final configuration for the Cisco ASA. You may use it on any compatible ASA devices.
- Cisco_ASA5506-X.virl – Cisco VIRL topology file with final lab configuration. It is fully configured lab based on the requirements in the article.
As part of our documentation effort, we maintain current and accurate information we provided. Documentations are routinely reviewed and updated. We ask for your email address to keep you notified when the article is updated.

Good article demonstrating the little amount of configuration required to get an ASA configured for use, you may want to include in the SSH section ‘aaa authentication ssh console LOCAL’ as I believe that is a requirement for SSH to authenticate after being enabled.
Good catch! I will make a note to add. Thank you.
Hello Jack, good article. By default, firepower don’t have to be enabled or configured, right? I have question about asa 5506x, currently we bought and tested it. We have Verizon fios for business with 29 static IP addresses, Verizon tech instruct me to use subnet mask of 255.255.255.0. and that’s working fine once I configure a labtop with any static IP Verizon provided. However, once I connect my asa to the Verizon network, it seems only one IP is working fine, that asa’s outside IP address. I added static NAT one by one, it doesn’t work. I believe it’s Verizon up stream routers don’t route traffic properly since once I turn on firewall log, there are no hits for all other IP addresses. I asked Verizon tech to route all public IP addresses they assigned to me to our asa’s outside interface IP, they told me that we cannot do static route for us. They blame this is my asa configuration issue. Is there any workaround for this?
Many thanks.
Harry
Harry, there is a simple test you can do to isolate the problem. Use the same laptop you used for testing, assign the static IPs that you are supposed to have, one by one to test. For example, Verizion provided you 123.123.123.65 – 79, you should be able to use any of these IPs in that range on your laptop to get to Internet. If that test fails, it is Verizon’s problem. If all IPs worked fine on your laptop, we’ll have to look into your ASA configuration. Hope it helps.
Hi Jack,
Thank you for your quick reply. Yes, I did one by one IP address test, it works fine. I enable proxy arp for NAT as well. It still doesn’t help.
Thanks,
Harry
I’ll need to see your ASA configuration to tell what’s wrong.
Hi Jack,
I have sent email to you.
Thank you.
Harry
Hi Harry,
This is a known problem in this region, Verizon’s equipment does an “illegal” ARP request from 0.0.0.0 which the ASA throws out.
A little more is at:
http://bilherd.mercury-cg.com/?p=84
Shouldn’t we better use object nat rules for nat from inside and dmz to the internet? With your suggested manual nat rules, we have to add a nat excemption for traffic between inside and dmz to make connections from inside to dmz and/or from dmz to outside possible.
An object nat rule for the inside network from inside to outside would be restricted to the traffic that will be send to outside according to the current routing table, the twice nat rule will force all matching traffic (independent from the routing table) to leave the asa through the destination interface given in the nat rule, i.e. in this case the outside interface … For identity nat rules, there is a “route-lookup” option, but this is only possible for identity nat …
Juergen, your configuration would work but I found it is much cleaner to configure manual NAT as described in this article. When you have a lot of NAT’ing rules, the configuration can get large and difficult to read and manage. In addition, manual NAT is much more flexible and you can apply the same concept to all NAT’ing situations. Hope it helps.
Nice article, Jack. One thing I think you might have missed is the physical cabling and interface setup of the firepower module… at least on a 5506.
Ryan, thanks for your suggestions. I’ll definitely incorporate physical cabling and interface setup in future articles.
Good artickel! I have one question:
If i want the description to WAN to get the ip by dhcp from the Provider
witch route outside 0.0.0.0 0.0.0.0 10.1.1.2 is to use?
Thank you!
Horst, in that case please use the configuration below. The ASA will automatically obtain an IP from your ISP and set default gateway to the ISP. No need to configure static route.
ASA#configure terminal
ASA(config)#interface GigabitEthernet1/1
ASA(config-if)#ip address dhcp setroute