Since Cisco’s acquisition of SourceFire in 2013, Cisco has incorporated one of the best leading Intrusion Prevention System (IPS/IDS) technologies into its “next-generation” firewall product line. Cisco’s ASA firewalls with Sourcefire’s FirePOWER Services are designed to provide contextual awareness to proactively assess threats, correlate intelligence, and optimize defenses to protect networks. I will walk you through step-by-step Cisco ASA 5506-X FirePOWER Configuration Example. The configuration also applies to the product family, ASA 5508-X, 5516-X and 5585-X.
If you are looking for best practice, baseline configuration of the ASA 5506-X before moving on to setting up the FirePOWER module, please read: Basic Cisco ASA 5506-x Configuration Example, or download configuration template for FREE.

Cisco ASA 5506-X FirePOWER Configuration Example
Introduction
Cisco ASA 5506-X with FirePOWER module is the direct upgrade path from legacy Cisco ASA5505. It incorporated the industry leading IPS technologies, provides next-generation Intrusion Prevention (NGIPS), Application Visibility and Control (AVC), Advanced Malware Protection (AMP) and URL Filtering. It is available in desktop model 5506-X, integrated wireless access point model 5506W-X and a ruggedized model 5506H-X for industrial control systems and critical infrastructure environment.
Major Differences Compared to Legacy ASA 5500s
- The new “X” models are running on multicore 64-bit processors compared with single core 32-bit processors on older ASA models.
- The “X” models have much higher CPU and Memory capacity, provide much higher traffic throughput compared to the same class. It has also made itself FirePOWER ready.
- The “X” models are next-generation firewalls. With subscription to additional licenses, you can have either Cloud based Web Security / Essentials or running local FirePOWER in software. (except for ASA 5585-X in hardware) The Cloud based security suite was Cisco’s legacy solution before adopting SourceFire solution. I recommend getting the FirePOWER option instead of the Cloud based solution, since it may be phased out in the near future.
- Routed interfaces instead of switched interface on the legacy ASA5505. The Cisco ASA5506-X has 8xGE routed interfaces, 1xGE MGMT, RJ45+USB mini console ports. It provides greater flexibilities of using physical interfaces (as opposed using sub-interfaces) to create multiple security zones using DMZ networks. This change is appreciated by medium to enterprise sized businesses customers. However for SOHO users who used to connect PCs directly to the ASA 5505, you will need to add a layer 2 switch on the LAN.
- The new ASA 5506W-X provides integrated Wireless Access Point, which is good for SOHO users. The ruggedized model 5506H-X, can be suitable for outdoor applications
- The new ASA 5506-X has a new interface naming conversion that starts from Gig1/1 instead of Gig0/0. I’m not sure why Cisco made such change, it only added unnecessary translation work for ones migrating from legacy models.

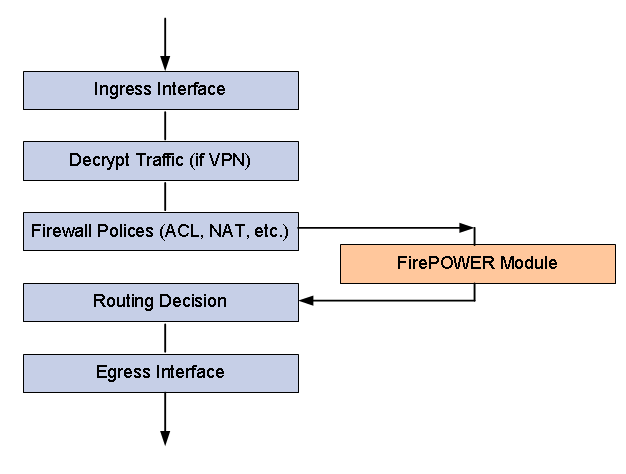
Traffic Flow
Similar to deploying a standalone IPS solution, the integrated FirePOWER module supports “inline” mode and “passive monitoring” mode. “Inline” mode provides additional benefits than monitoring mode. FirePOWER deployed in “inline” mode provides best case deep inspection analysis before packets are returned to the ASA main plane. It proactively takes action when malicious traffic is detected.
When traffic enters ASA’s ingress interface:
- The ASA decrypts the traffic if it was part of an established VPN tunnel.
- Packets are checked against firewall policies such as ACL, NAT and Inspection.
- Optionally, traffic is sent to the FirePOWER Module for deeper level inspection. You may configure to send all traffic or only high risk traffic to the FirePOWER module to conserve system resources.
- Traffic passed FirePOWER inspection is returned to the ASA main engine for next step routing decision.
- Traffic is then passed to the ASA’s egress interface to be forwarded to the rest of the network.
Licensing Options
In order to utilize any of the ASA’s next-generation firewall features, Cisco made customers order subscription based licenses for the FirePOWER module to work. The subscription based licenses can be purchased annually, 3 or 5 years with discount. Here are list of licenses available:
- Intrusion detection and prevention (IPS license)
- Application Visibility and Control (AVC)
- File control and advanced malware protection (AMP)
- Application, user, and URL control (URL Filtering)
- IPS license is required for the AVC, AMP and URL Filtering license.
Management Options
Even though the FirePOWER module is integrated in to one ASA platform, it is managed separately from the ASA configuration. You have two options of managing and operating the FirePOWER module- Distributed management model and Centralized management model.
Distributed model using ASDM: For standalone single site deployment.
Suitable for SOHO customers who do not have more than 3 locations and do not want to manage a separate sever infrastructure.
Centralized model using FirePOWER Management Center
The Management Console is a hardware or virtual appliance installed centrally to manage multiple FirePOWER deployments at same time. Suitable for enterprise customers who have more than 5 locations deployed with FirePOWER.
If you are looking for best practice, baseline configuration of the ASA 5506-X before moving on to setting up the FirePOWER module, please read: Basic Cisco ASA 5506-x Configuration Example, or download configuration template for FREE.
Continue reading:
Cisco ASA 5506-X FirePOWER Configuration Example Part 2
Configure and Manage ASA FirePOWER Module using ASDM Part 3
Configure and Manage ASA FirePOWER Module using Management Center Part 4

Hello,
I have an ASA 5516-X box and I meet a strange situation, when I rediret all traffic to FirePOWER using:
class-map global-class
match any
policy-map global_policy
class global-class
sfr fail-open
all my outbound traffic is blocked, the only solution I found is to go to Configuration \ Firewall \ Service Policy Rules – global-class (Rule Actions \ ASA Inspection Firepower – and put in check “Enable Monitor only”)
Do you have any idea?
Thanks in advance!
Daniel
Hi Daniel, I have seen similar issues in the past. It is generally caused by one of these two things.
1. Make sure you have activated the FirePOWER licenses on the unit. If you have pair of ASAs in HA cluster, both ASAs must carry valid FirePOWER licenses and activated on both units. Make sure FirePOWER configurations on both ASAs are in sync as well.
2. In FirePOWER configuration, go to Policies>Access Control. Make sure you have configured an Access Control Policy, and nothing in there could potentially block all traffic. The Default Action on the bottom sends filtered traffic to a Intrusion Policy. If you use the default Intrusion Policy it should not block general internet access.
Among these two I have seen the first one most. Let me know how it goes.
Hi Jack,
Thanks for your excellent tips!
As you recommend, I first checked the licenses. Are all valid (Protection, Control, URL Filtering and Malware). This is what I did next:
1. Configuration\Firewall\Service Policy Rules – global-class (Rule Actions \ ASA Inspection Firepower – unchecked “Enable Monitor only”)
Result: Outgoing traffic was blocked again.
2. FirePOWER Configuration\Policies\ACP – I created a new policy “Allow All” with a Standard Rule that allow all traffic
Result: Outgoing traffic is permitted.
I want that FirePOWER block all Social and Gambling urls. Do you know, it will be ok if I insert into that policy another Standard Rule which block the Social and Gambling access using “URLs” filter?
Or is better to create a second Policy only for denied Social and Gambling urls?
Thanks again!
Daniel.
Hi Daniel,
It is hard to say without looking into your specific configuration. Can you send me a message using the contact form on the site and I will respond back with my email. Thanks!